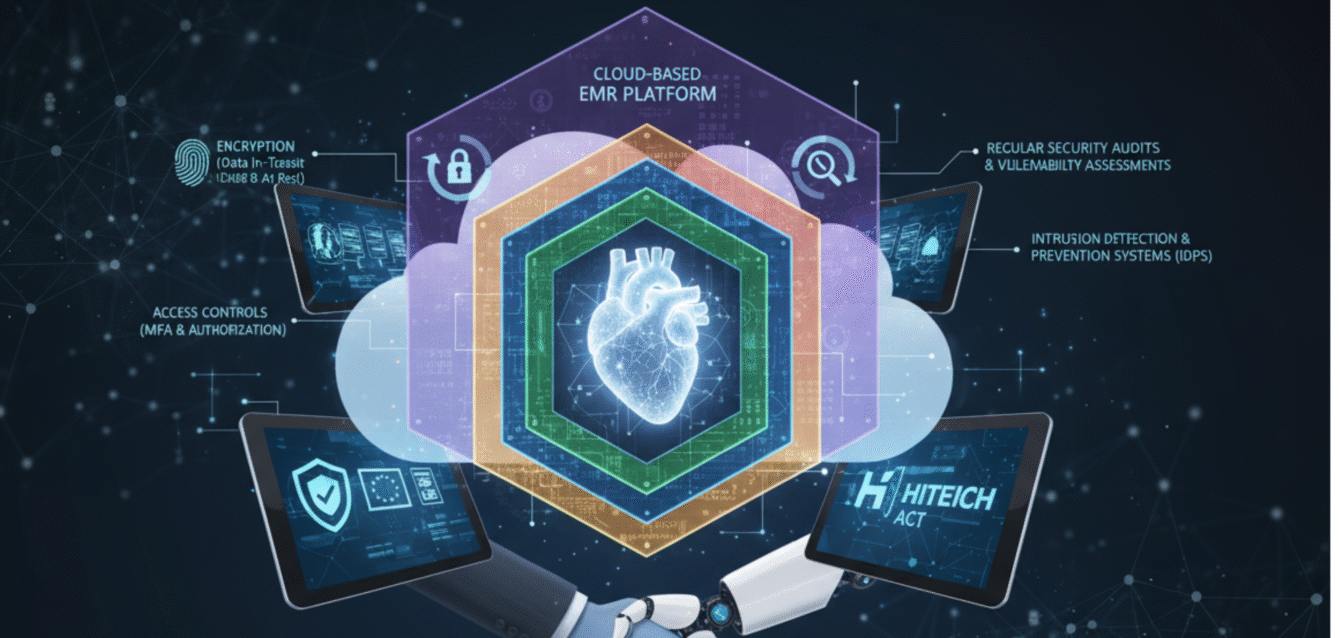
In a digital‑first healthcare environment, patient records are no longer locked in file cabinets or passed as paper charts— they exist across clouds, tablets, mobile devices and remote connections. While this transition unlocks immense benefits—faster access, shared workflows, telehealth integration—it also opens the door to serious responsibilities. Ensuring data security and regulatory compliance in cloud‑based electronic medical record (EMR) systems is not optional; it’s foundational to patient trust, clinical safety, financial integrity and organisational reputation. Without robust safeguards, a breach could lead to identity theft, diagnostic errors, regulatory fines, lawsuits or loss of accreditation.
By treating cloud EMRs as not only clinical tools but data guardians, healthcare organisations move from reactive protection to proactive assurance.
Who Gets to See What—and How Role‑Based Access Safeguards Patient Data
Cloud EMR systems must enforce a principle of least privilege. That means each user—doctor, nurse, receptionist, lab technician—only accesses the data essential for their role. Role‑Based Access Control (RBAC) prevents unnecessary exposure of sensitive data and limits damage if credentials are compromised. Studies show that strong RBAC combined with multi‑factor authentication (MFA) significantly reduces unauthorized access incidents.
In practice, a well‑configured EMR platform defines permissions by role, department, and context (on‑site vs remote). It automatically restricts access to specific patient records, logs every access attempt, locks down sensitive fields, and segments user‑profiles across modules. When an audit or incident occurs, the log shows who accessed what, when and why—providing full traceability. In effect, access control becomes not just a feature but the first line of defence in protecting patient privacy.
Encryption, Secure Back‑ups, and Protecting Data in Transit and at Rest
Encryption is a core safeguard for cloud‑based EMRs—covering data at rest (on disks or in the cloud storage) and data in transit (between client devices, mobile apps, and cloud servers). Without it, sensitive health information remains vulnerable to interception or theft. One overview of healthcare cloud‑data best practices emphasises end‑to‑end encryption, secure backups, real‑time threat monitoring and rigid authentication.
Effective systems apply layered encryption strategies: symmetric encryption of stored data, TLS or equivalent for data in transit, hardware‑based key management, and immutable backups that prevent tampering or ransomware encryption. They also perform regular backup snapshots in encrypted form, store them in geographically separate regions, and ensure rapid restoration under disaster‑recovery plans. These protections ensure that even if an attacker penetrates a layer, the patient data remains encrypted and inaccessible.
Regulatory Compliance: Audit Trails, Data Retention and Standards
Cloud EMRs must satisfy highly regulated frameworks such as HIPAA in the US, GDPR in Europe, as well as other local data‑protection laws and healthcare‑specific standards. But compliance isn’t a one‑time checklist—it’s an ongoing process. Proper systems utilise audit trails that record every access, modification, deletion, and transfer of patient records—timestamped, user‑identified, and immutable. These logs serve both as security tools and regulatory evidence.
Retention policies also matter: how long must records be held, when must they be archived or deleted, and how are patient consents managed when data moves across borders or systems? Standards like ISO 27001/27017/27018 address information‑security management and cloud‑specific data protection scenarios. A compliant system aligns data‑governance, user training, incident‑response plans and vendor‑management structures to meet regulatory audits, patient‑data subject requests and cross‑border data transfer rules.
Managing Shared Responsibility in the Cloud Environment
Cloud‑based EMR platforms operate within a shared responsibility model: the technology provider ensures infrastructure security, physical data‑centre protection and platform‑integrity—but the healthcare provider remains responsible for configurations, access control, data classification and user training. If permissions are misconfigured, or passwords are weak, the system remains vulnerable despite robust infrastructure. Cloud‑security frameworks emphasise that encryption, zero‑trust access, regular audits and vendor‑due‑diligence must be embedded in provider‑processes.
For healthcare organisations, this means establishing clear governance: mapping responsibilities, performing vendor assessments, ensuring service‑level agreements (SLAs) include data‑protection obligations, monitoring service‑provider compliance reports, and scheduling regular security reviews. By clarifying ownership of each layer—platform, network, application, data—the organisation avoids blind zones. In doing so, it turns the cloud‑environment from a risk into a resilient and trusted system.
Addressing Cloud‑Specific Threats: Insider Risk, Vendor Access, and Multi‑Tenant Platforms
Unlike on‑premises systems, cloud EMRs often run in multi‑tenant or shared environments, bringing additional threats such as insider misuse (by vendor staff or partner organisations), weak cross‑tenant isolation and supply‑chain attacks. Healthcare organisations must treat these risks seriously. Effective defence combines strong user‑authentication, least‑privilege vendor access, compartmentalised data storage, and monitoring tools that detect anomalous activity. A recent review of cloud‑data protection emphasises that identity and access management (IAM), immutable backups and threat detection systems are key for healthcare‑cloud deployments.
In operational terms, this means the EMR provider should log vendor access, support role‑segregation for vendor vs internal users, encrypt data at rest with customer‑managed keys, and support data‑export controls for moving out of the system. It also means the healthcare provider must conduct periodic audits of vendor access logs, request SOC 2 or ISO‑certification reports, and ensure contractual right to audit. These steps mitigate risks unique to cloud platforms, maintaining assurance over the full lifecycle of patient data.
Routine Reviews, Staff Training and Cyber Hygiene That Support Compliance
Even the most advanced technical platform fails if staff forget basic cyber‑hygiene. Training medical, administrative and support teams on security best practices—strong passwords, phishing awareness, correct access‑request flows, remote‑login protocols—is essential. A cloud‑security summary for healthcare emphasises routine training, MFA enforcement, regular patching and threat‑detection automation.
Training should cover incident‑response steps, how to handle data‑subject access requests, proper use of authentication tokens, how to spot social‑engineering attempts, and how to report a potential breach. Combined with routine review of access logs, third‑party penetration tests, and internal simulations of threat scenarios, these human‑factors programmes ensure that compliance is not just technology‑led but culture‑driven. When staff feel accountable and aware, data security becomes part of everyday operations.
Monitoring Improvements and Demonstrating Compliance in Practice
In a regulated environment, compliance isn’t just about setting policies—it’s about demonstrating results. Healthcare organisations must establish metrics and dashboards that show security posture, incident‑response times, audit‑log completeness, access‑failure trends, number of patches installed, data‑exfiltration attempts blocked, and user‑access anomalies. These measurable indicators demonstrate that cloud‑based EMR systems are not just secure in theory but in practice. A strong audit trail system, for instance, allows leadership to review “who accessed what” and “when” and to respond to suspicious patterns.
By reviewing these metrics monthly, aligning them with board‑level risk dashboards, and tying them to operational investment decisions—such as increasing vendor review frequency, upgrading encryption, or adding threat‑monitoring tools—the healthcare provider ensures that data security and compliance aren’t static goals but evolving capabilities. Continuous measurement also supports regulatory audits, vendor‑assessments and error‑trend detection—all of which strengthen trust internally, with patients and with regulators.
The Takeaway
Data security and compliance in cloud‑based EMRs demand more than technology—they demand holistic governance, strong access controls, encryption, continuous monitoring, staff engagement and measurable results. When these elements align, healthcare organisations not only meet regulatory demands but build trust, safeguard patients and unlock the full potential of digital records.